Last month, a marketing director saw her open rates plummet from 28% to 11% overnight. Her messaging and content remained unchanged. Yet, mailbox providers had quietly updated their filters, sending her messages to spam folders across thousands of inboxes.
This scenario is a daily reality for businesses in 2026. Despite generating $36 to $45 in returns for every dollar spent, reaching the inbox has become much harder. Major providers now enforce stricter sender requirements than ever before.

The landscape has fundamentally shifted. Success is no longer about clever tactics or high send volumes. Instead, email deliverability now hinges on technical excellence, authentic subscriber relationships, and respect for audience preferences.
We're entering an era where AI-powered filters evaluate our entire sending reputation. Authentication protocols like SPF, DKIM, and DMARC are now mandatory. Engagement signals now outweigh message frequency, and deliverability performance requires a systematic approach. This approach must cover infrastructure, content quality, and ongoing optimization.
Understanding the 2026 Email Marketing Landscape
Before we dive into tactical improvements, we need to grasp the fundamental shifts in email marketing by 2026. The relationship between senders and email providers has evolved significantly. Today, providers act as gatekeepers, safeguarding their users' experience, not just delivering emails.
Platforms like Gmail, Outlook, and Yahoo employ sophisticated machine learning algorithms. These systems scrutinize sender behavior, content quality, and recipient interactions. The era of sending bulk emails and hoping for the best is over.
Our email campaign performance now hinges on engagement metrics, not volume. Metrics like opens, clicks, replies, and forwards indicate positive engagement with each email provider. On the other hand, deletions without reading, spam complaints, and prolonged inactivity harm our sender reputation.
Several key changes define the emailing environment in 2026:
- AI-assisted filtering evaluates content quality, tone, and historical sender patterns automatically
- Engagement signals carry more inbox weight than send volume or frequency
- Privacy and consent expectations have increased dramatically with stricter enforcement
- First-party lists significantly outperform third-party and purchased contact databases
- Authentication protocols like SPF, DKIM, and DMARC are now mandatory for serious senders

Yahoo and Microsoft now enforce authentication and consent standards for bulk senders. These standards include stricter complaint tolerance and one-click unsubscribe expectations. Low engagement segments can drag down domain reputation, even with technical compliance.
Privacy regulations have tightened across multiple jurisdictions. GDPR, CAN-SPAM, and CCPA enforcement impose legal consequences for poor list management. Purchasing lists or adding contacts without explicit consent results in immediate deliverability issues and legal risks.
The competitive landscape has become more intense. Professionals receive over 120 emails daily in 2026. Our messages must be exceptionally relevant and valuable to stand out.
Grasping these dynamics is critical for boosting our email campaign performance. Every strategy we implement builds on this foundational knowledge of modern email ecosystems. The inbox now belongs to the subscriber, and our task is to earn our place through consistent value delivery and respectful emailing practices.
Step 1: Build and Maintain a Verified Email List
Before diving into crafting compelling subject lines or designing beautiful templates, we must first establish a verified, high-quality email list. The quality of our subscriber list is the cornerstone of our email marketing success. A large list filled with invalid addresses can damage our sender reputation and waste resources. On the other hand, a smaller list of engaged, verified contacts consistently delivers stronger results.
Understanding that list quality always outperforms list size is key. Industry data reveals that email lists naturally decay by approximately 22% per year. This decay is due to people changing jobs, abandoning old addresses, or switching providers. We cannot simply collect addresses and assume they remain valid indefinitely.
Our approach to building a verified email list must begin at the moment someone subscribes and continue throughout their entire relationship with our brand. This systematic approach protects our sender reputation while ensuring our messages reach people who genuinely want to receive them.
Implementing Email Verification from the Start
The most effective time to verify an email address is at the point of signup. When we implement real-time verification during the subscription process, we catch problems before they enter our database. This proactive approach prevents invalid addresses, typos, and temporary emails from ever becoming part of our list.
Real-time email verification checks multiple factors instantly. The system validates syntax formatting, confirms domain existence, and verifies that the mailbox can receive messages. This entire process happens in milliseconds, providing immediate feedback to subscribers if they've made an error.
For high-impact lists or regulated industries, we strongly recommend implementing double opt-in procedures. This method requires subscribers to confirm their email address by clicking a verification link sent to their inbox. While it adds an extra step, double opt-in dramatically reduces fake signups and ensures subscribers genuinely want our content.
Using an Online Email Verification Tool
An online email verification tool provides the technology infrastructure we need to validate addresses automatically. These tools integrate directly with our signup forms, working behind the scenes to assess each email address as it arrives. The best solutions check for several risk factors simultaneously.

When evaluating an online email verification tool, we should look for these essential capabilities:
- Syntax validation: Identifies formatting errors and typos in email addresses
- Domain verification: Confirms the domain exists and has valid MX records
- Mailbox checking: Verifies the specific email account can receive messages
- Spam trap detection: Flags known spam trap addresses before they enter our list
- Disposable email detection: Identifies temporary email services used for one-time signups
The verification process should also identify role-based emails like info@, admin@, or support@. These addresses typically belong to multiple people or departments, which can negatively impact engagement metrics and sender reputation.
Choosing Between Email Verification Software and Email Verification SaaS
We face an important decision when selecting our verification approach: should we use email verification software installed on our own servers, or opt for email verification SaaS delivered through the cloud? Each option offers distinct advantages depending on our technical capabilities and business requirements.
Email verification software runs on our own infrastructure. This gives us complete control over our data and verification processes. Organizations with strict data privacy requirements or complex compliance needs often prefer this approach. It requires technical expertise to install, configure, and maintain the system.
On the other hand, email verification saas provides immediate access through cloud-based platforms. These services handle all infrastructure management, security updates, and database maintenance. We simply integrate their API into our systems and begin verifying addresses immediately.
For most organizations, online email verification software delivered as a SaaS solution offers the best balance of accuracy, speed, and ease of implementation. These platforms typically provide:
- Automatic updates to spam trap databases and validation rules
- Scalable infrastructure that grows with our list size
- Enterprise-grade security without internal maintenance
- Transparent pricing based on verification volume
- Integration support for popular email platforms
The choice ultimately depends on our technical resources, budget, and data governance policies. Companies with in-house development teams and strict data residency requirements may prefer self-hosted software, while organizations seeking faster deployment typically choose SaaS solutions.
Conducting Regular Email Validation
Even after implementing verification at signup, we must conduct ongoing email validation throughout our list's lifecycle. Email addresses that were valid six months ago may no longer work today. People change jobs, companies rebrand with new domains, and email accounts get abandoned.
Regular validation helps us identify addresses that have become invalid over time. This proactive maintenance prevents delivery failures and protects our sender reputation. A healthy bounce rate should remain under 2%, and consistent validation helps us achieve this benchmark.
We should establish a regular cleaning schedule based on our sending frequency. Organizations that send daily emails need monthly validation, while those with less frequent campaigns might validate quarterly. The key is consistency, not perfection.
Setting Up Automated Online Email Validation
Manual list cleaning becomes impractical as our subscriber base grows. Automated online email validation solves this challenge by continuously monitoring our list quality without requiring constant human intervention. These systems work in the background, flagging problematic addresses for our review.
When setting up automation, we configure the system to scan our entire database on a predetermined schedule. The online email validation process categorizes each address into risk levels:
- Valid: Addresses confirmed to accept mail with no known issues
- Risky: Addresses that might cause problems, including role-based or catch-all emails
- Invalid: Addresses confirmed as non-existent or permanently disabled
- Unknown: Addresses that couldn't be verified due to server restrictions
Our automated system should also track engagement patterns. Subscribers who haven't opened or clicked in 90-180 days represent growing deliverability risks. We need to implement sunset policies that automatically flag these inactive contacts for re-engagement campaigns or suppression.
Removing Invalid and Risky Addresses
Once our validation process identifies problematic addresses, we must take decisive action. Keeping invalid addresses on our list serves no purpose and actively damages our email campaign performance. Different types of invalid addresses require different removal strategies.
Hard bounces result from permanent delivery failures. These occur when an email address doesn't exist or the domain is invalid. We should remove hard bounces immediately after the first bounce. There's no reason to attempt delivery again.
Soft bounces indicate temporary delivery problems like full inboxes or server issues. We should retry soft bounces several times over a few days. If the address continues to soft bounce after multiple attempts, it becomes a candidate for removal.
Beyond bounces, we need to address other risky address types:
- Spam trap addresses that could blacklist our sending domain
- Known complainers who frequently mark emails as spam
- Disposable email addresses used only for initial signup offers
- Role-based emails that show low engagement rates
The data clearly shows that keeping everyone on our list forever is not a viable strategy. We must accept that some subscribers will naturally leave our audience over time, and removing them actually improves our overall performance.
Managing List Hygiene Best Practices
Maintaining a clean, engaged email list requires ongoing attention to hygiene best practices. These procedures work together to ensure our list remains healthy and our campaigns continue performing well. We need to establish regular routines that become part of our standard operating procedures.
First, we should monitor our list growth rate versus decay rate. Healthy lists show net positive growth even after removing inactive subscribers. If our decay rate exceeds our growth rate, we need to examine both our acquisition strategies and our content relevance.
Second, we must segment our list based on engagement levels. Active subscribers who regularly open and click deserve different treatment than those who haven't engaged in months. This segmentation allows us to send re-engagement campaigns to at-risk subscribers before removing them entirely.
Third, we should implement clear suppression rules based on subscriber lifecycle length. Organizations with short sales cycles might use a 6-month sunset rule, while those with longer cycles might extend this to 9 or 12 months. The specific timeframe matters less than having a consistent policy.
Our list hygiene checklist should include these monthly tasks:
- Review bounce reports and remove hard bounces immediately
- Analyze engagement trends and identify declining segments
- Run re-engagement campaigns for subscribers inactive 90+ days
- Suppress or remove subscribers inactive beyond sunset threshold
- Monitor complaint rates and investigate any sudden increases
- Verify that new signups match expected quality and source patterns
We also need to provide transparent opt-in experiences that clearly state our email frequency and value proposition. When subscribers know what to expect, they're more likely to remain engaged and less likely to mark our emails as spam.
Remember that a smaller, engaged list dramatically outperforms a large, unengaged one. Email providers prioritize sender reputation based on engagement signals. Ten thousand engaged subscribers will generate better deliverability and ROI than 100,000 disengaged contacts.
By using proper email verification practices from signup through the entire subscriber lifecycle, we protect our sender reputation and ensure our messages reach people who actually want them. This foundation makes every subsequent optimization effort more effective and sustainable.
Step 2: Configure Essential Email Authentication Protocols
Yahoo and Microsoft now enforce authentication requirements aggressively, making SPF, DKIM, and DMARC setup non-negotiable for bulk senders. These three protocols work together to verify your identity and protect your domain from spoofing attacks. Without proper authentication, inbox providers will automatically flag your messages as suspicious or reject them entirely.
Authentication earns us the right to compete for inbox placement in 2026. We must use a branded domain instead of a generic email service provider domain to build our reputation. This technical foundation proves we are legitimate senders and separates us from spammers who cannot meet these IETF standards.
Setting Up SPF Records in Your DNS
SPF creates a whitelist of IP addresses authorized to send email on behalf of our domain. This DNS-based protocol prevents malicious actors from forging our sender address. We need to configure our SPF record correctly to maintain strong email deliverability.
The Sender Policy Framework tells receiving servers which mail servers are legitimate sources for our domain. When an email arrives, the recipient's server checks our SPF record to verify the sending IP address appears on our approved list. Failed SPF checks immediately hurt our sender reputation.
Creating Your SPF Record
We start by accessing our domain's DNS management console through our hosting provider or domain registrar. The SPF record appears as a TXT record in our DNS settings. A basic SPF record follows this format: v=spf1 include:emailprovider.com ~all.
We must list all legitimate sending sources in our SPF record. This includes our email service provider, marketing automation platform, and any third-party services that send on our behalf. Each source requires an "include" statement or IP address specification.
The SPF protocol has a critical limitation: 10 DNS lookups maximum. We need to consolidate our sending sources efficiently to stay within this limit. Too many lookups cause our SPF record to fail validation entirely.
Here are the key components we include in our SPF record:
- Version declaration (v=spf1) at the beginning
- Include statements for authorized email providers
- IP4 or IP6 addresses for dedicated sending servers
- Qualifier mechanism (~all, -all, or ?all) at the end
- Optional modifiers for redirect or explanation
Testing SPF Configuration
After publishing our SPF record, we verify it works correctly using specialized testing tools. MXToolbox provides a free SPF checker that validates our record syntax and counts DNS lookups. Google's Admin Toolbox offers another reliable testing option.
We send test emails to seed addresses at major providers like Gmail, Outlook, and Yahoo. Then we examine the email headers to confirm SPF passes authentication checks. The authentication results appear in the "Received-SPF" header field.
Regular SPF monitoring catches configuration errors before they impact email deliverability. We should retest whenever we add new sending services or change email infrastructure. This proactive approach prevents authentication failures that damage our sender reputation.
Implementing DKIM Email Signing
DKIM adds a digital signature to our email headers that proves messages haven't been tampered with during transit. This cryptographic authentication method uses public-key encryption to verify email integrity. Receiving servers decrypt the signature using a public key we publish in our DNS records.
The DKIM signature covers specific email elements including the message body, subject line, and key headers. Any modification to these signed elements causes signature validation to fail. This protection ensures recipients receive exactly what we sent.

Our email service provider typically generates DKIM keys through their administration interface. The system creates two components: a private key that remains secure on the sending server and a public key for DNS publication. We should use 2048-bit RSA keys for maximum security.
Each DKIM key includes a selector that allows us to maintain multiple keys simultaneously. The selector appears in the DNS record name and the email signature header. We rotate keys periodically to maintain security and can test new keys before switching production traffic.
Most platforms offer step-by-step wizards for DKIM setup. We follow their specific instructions to generate keys properly formatted for our email infrastructure. The process takes only a few minutes but provides essential authentication protection.
Adding DKIM to Your DNS
We publish our DKIM public key as a TXT record in our DNS zone. The record name follows this pattern: selector._domainkey.yourdomain.com. The selector matches what we configured in our email service provider settings.
The DKIM record value contains our public key along with version and key type specifications. We copy this value exactly as provided by our email platform. Even small errors in the DNS record prevent DKIM validation from working.
DNS propagation takes anywhere from minutes to 48 hours. We wait for full propagation before sending production emails. Testing tools verify our DKIM record is accessible and properly formatted for authentication checks.
Establishing DMARC Policies
DMARC ties SPF and DKIM together by telling receiving servers what actions to take when authentication fails. This policy-based protocol provides visibility into who sends email claiming to be from our domain. We gain valuable reporting data while protecting our brand from spoofing.
Our DMARC policy appears as another TXT record at _dmarc.yourdomain.com. The policy specifies three possible actions: none (monitoring only), quarantine (send to spam), or reject (block delivery). We also configure reporting addresses to receive authentication failure notifications.
We recommend starting with a p=none policy to collect data without affecting email delivery. This monitoring phase reveals authentication issues we need to fix. After confirming our SPF and DKIM work correctly, we gradually move to p=quarantine and eventually p=reject for maximum protection.
DMARC alignment requires either SPF or DKIM to pass and match our From domain. This alignment check prevents sophisticated spoofing attacks that might pass one authentication method. Both Yahoo and Microsoft now require DMARC policies for high-volume senders.
Key DMARC policy components include:
- Policy directive (p=none, p=quarantine, or p=reject)
- Subdomain policy (sp=) for different treatment of subdomains
- Alignment mode for SPF and DKIM (relaxed or strict)
- Reporting addresses (rua= for aggregate, ruf= for forensic)
- Percentage tag (pct=) for gradual policy rollout
Ensuring IETF Standards Compliance
The Internet Engineering Task Force sets technical specifications for email protocols that we must follow. IETF standards cover everything from message formatting to authentication implementation. Compliance ensures our emails work correctly across all receiving systems.
RFC 5322 defines proper email message structure including header fields and body content. We format our emails according to these specifications to avoid parsing errors at receiving servers. MIME encoding standards (RFC 2045-2049) govern how we handle attachments and HTML content.
We send from a dedicated subdomain like mail.ourdomain.com instead of our primary domain. This isolation protects our main domain reputation if email issues arise. The subdomain should have its own SPF, DKIM, and DMARC records configured independently.
Consistent sender identity matters a lot for authentication and reputation. We maintain predictable sending patterns and avoid sudden volume spikes. When increasing volume or mailing cold lists, we warm our IPs gradually to build trust with inbox providers.
Authentication protocol maintenance requires ongoing attention. We monitor our DNS records for expiration or unauthorized changes. Any gaps in SPF, DKIM, or DMARC coverage immediately impact our email deliverability and sender reputation scores.
Step 3: Avoid Spam Traps and Maintain Sender Reputation
Accidental hits on spam traps can destroy your email deliverability overnight. These honeypots, set by anti-spam groups and providers, identify questionable senders. Understanding and avoiding these traps is essential.
Spam traps are a serious threat, signaling poor list management. Sending to these addresses triggers penalties, blocking your campaigns. Your sender reputation is at risk with every campaign.
Understanding Different Types of Spam Traps
Spam traps vary, each indicating different issues with your email practices. Recognizing these types is key to effective prevention.
Anti-spam groups and providers strategically place these traps. They monitor who sends to them, identifying those who cut corners. Knowing the types helps diagnose list acquisition failures.
Pristine Spam Traps
Pristine spam traps are the most dangerous. These addresses never belonged to real people and were created to catch bad actors. Spamhaus and others publish these addresses online.
Several risky channels can lead to pristine traps:
- Purchased or rented email lists from third-party vendors
- Email addresses scraped from websites using automated tools
- Lists obtained through unethical harvesting methods
- Addresses embedded in online directories or forums
Hitting a pristine spam trap proves you obtained addresses illegitimately. Email providers swiftly block your domain upon such violations.

Recycled spam traps were once legitimate addresses. After abandonment, providers wait 12 to 18 months before converting them into traps. These traps show poor list hygiene, not illegitimate acquisition.
While less severe than pristine traps, recycled trap hits harm your deliverability. Providers see these as signs of neglect in list maintenance. Regularly removing inactive subscribers is critical.
Consequences of recycled trap hits include declining deliverability. Accumulating these violations over time damages your reputation.
Monitoring Spamhaus and Major Blocklists
Spamhaus is a leading anti-spam organization. Email providers worldwide consult their blocklists. Regularly checking your status is essential.
Spamhaus maintains several critical blocklists:
- SBL (Spamhaus Block List) - Lists known spam operations and sources
- XBL (Exploits Block List) - Identifies hijacked computers and malware sources
- PBL (Policy Block List) - Flags IP addresses that shouldn't send email directly
Beyond Spamhaus, monitoring Barracuda, SORBS, and SpamCop is vital. Each has its own criteria and delisting procedures. Automated blocklist checking services alert us to any issues.
Weekly checks using blocklist monitoring tools are recommended. This proactive approach helps identify and address issues before they harm our campaigns. Early detection leads to faster resolution and less damage to our reputation.
Removing Yourself from Blocklists
Discovering your domain or IP on a blocklist requires immediate action. Requesting removal without fixing the issue is futile. Blocklist operators demand evidence of problem resolution before delisting.
Follow this systematic approach for removal:
- Investigate the root cause - Determine what triggered the listing (spam trap hits, complaint rates, compromised accounts)
- Implement corrective measures - Fix the identified issues before requesting delisting
- Document your remediation - Prepare clear explanations of what went wrong and what steps were taken
- Submit delisting requests - Complete the specific delisting process on the blocklist operator's website
- Provide supporting evidence - Include documentation showing permanent resolution of the problem
Some blocklists automatically remove entries after clean sending behavior. Others require manual review. Spamhaus typically requires concrete changes before removal.
Response times vary among blocklists. Removal can happen in hours or take days. Thorough and patient remediation efforts yield better results than rushing.
Preventing Future Spam Trap Hits
Prevention is the best strategy for maintaining email deliverability. Once hit, recovery is time-consuming. Implementing multiple protective layers is essential.
Our prevention strategy includes:
- Implement email verification at signup - Validate addresses in real-time to catch typos and fake entries immediately
- Require double opt-in confirmation - Send verification emails that subscribers must click to confirm their subscription intent
- Establish aggressive sunset policies - Remove subscribers after 90 to 180 days of complete inactivity, well before addresses become recycled traps
- Never purchase or rent email lists - Build our list organically through legitimate opt-in methods only
- Validate lists regularly - Run our entire database through reputable email validation services quarterly
Monitoring engagement metrics closely is critical. Subscribers who haven't engaged in months pose significant risks. Either re-engagement campaigns or removal from active lists is necessary.
Consistent sending patterns without sudden spikes are also important. Sudden volume increases trigger scrutiny from providers. They assume these spikes indicate purchased lists or compromised accounts, leading to heightened filtering.
Our sender reputation relies on these proactive measures. Spam trap hits can quickly destroy the reputation we've built. Focusing on quality and maintaining impeccable list hygiene ensures consistent delivery to subscriber inboxes.
Step 4: Optimize Your SMTP Configuration and Email Infrastructure
Our email infrastructure is like a hidden network that carries messages to subscribers worldwide. The technical setup we choose affects whether our campaigns reach their destination or hit roadblocks. Optimizing our SMTP configuration is key to supporting all deliverability efforts.
Simple Mail Transfer Protocol is the backbone of email delivery across the internet. Without proper setup, even well-crafted emails can fail to reach their destination. We must focus on several technical layers to ensure successful delivery.
Choosing an Email Service Provider for Reliable Infrastructure
Our first decision is picking the right email provider for our sending needs. This choice impacts our deliverability, from IP reputation to technical support. We need to evaluate providers based on essential criteria for campaign success.
Dedicated email service providers like SendGrid, Mailgun, and Amazon SES offer optimized infrastructure. They provide reputation management tools, analytics, and scalability. For transactional emails, specialized providers offer high-priority routing and advanced monitoring.
When evaluating providers, look at their delivery rates across major inbox providers. We need transparency on IP pool management and whether we'll use shared or dedicated IPs. The email provider should support SPF, DKIM, and DMARC records easily.
Customer support quality is critical when deliverability issues arise. We want providers with responsive technical teams. Real-time monitoring dashboards and detailed bounce reports help identify problems quickly.
Technical Settings That Maximize Inbox Placement
After selecting our infrastructure partner, proper SMTP configuration is essential. Multiple technical parameters must align for optimal deliverability. Each setting sends signals about our professionalism and security.

Port selection is a fundamental SMTP configuration decision. Modern email infrastructure relies on specific ports for security and compatibility. We should use port 587 with STARTTLS encryption for standard email submission.
Port 587 initiates connections as plaintext but upgrades to encrypted communication through STARTTLS. This approach balances security with compatibility. Port 465 offers SMTP over SSL for providers requiring this configuration.
We should avoid port 25 for email submission due to ISP blocking. Port 25 is the standard for server-to-server communication but signals security risks when used for client submission. Encryption through TLS protects our message content during transit.
Authentication Methods
Proper authentication proves our authorization to send emails from our domain. We need to configure valid SMTP credentials including username and password. These credentials should be stored securely using environment variables or encrypted configuration files.
Regular credential rotation enhances security by limiting exposure if credentials become compromised. We should implement proper timeout settings to handle temporary delivery delays. Our configuration must include retry logic for soft bounces and bounce handling mechanisms.
Authentication failures signal serious problems to inbox providers. When our credentials don't match or authentication fails, receiving servers may reject our messages. Regular testing ensures our authentication continues working correctly.
Monitoring Protocols for Delivery Verification
Understanding POP3 and IMAP helps us monitor message delivery and verify inbox placement. While these protocols retrieve emails, we can leverage them for delivery testing. They provide insights into how our campaigns appear to actual recipients.
We can use IMAP access to maintain seed lists, test accounts across major providers. This allows us to verify that our messages reach inboxes correctly. IMAP offers advantages over POP3 because it maintains messages on the server and syncs across multiple devices.
Some advanced marketers create monitoring systems that use IMAP to automatically access test mailboxes after each campaign. These systems verify delivery timing, check spam folder placement, and capture screenshots of how emails render. This proactive monitoring catches deliverability problems before they affect our entire list.
Building Reputation Through Strategic Volume Scaling
Managing IP reputation and warming is critical when launching new email programs or scaling volume significantly. Email providers track the reputation of sending IP addresses meticulously. New or dormant IPs have no established reputation, making sudden high-volume sending extremely risky.
We must implement IP warming by starting with our most engaged subscribers and sending small volumes initially. On day one, we should send only 50-100 emails to recipients who recently opened or clicked our messages. Then we gradually increase by 50-100% each day over 4-6 weeks until we reach our target volume.
This gradual approach allows us to build positive reputation signals like opens, clicks, and low complaint rates before sending to our full list. The reputation we establish during warming determines our long-term deliverability success. Rushing this process risks triggering spam filters and damaging our sender reputation permanently.
For shared IP addresses, common with smaller senders, we rely partly on our email provider's collective reputation. We must warm our domain reputation through gradual volume increases. With dedicated IPs, we have complete control but full responsibility for reputation management.
We should monitor our IP reputation using services like Sender Score, Google Postmaster Tools, and Microsoft SNDS regularly. These tools provide early warning signals about reputation declines that indicate developing deliverability problems. Watching these metrics helps us respond quickly before issues become severe.
Recovery from reputation damage requires consistent clean sending over weeks or months. Prevention through proper warming and ongoing monitoring protects the infrastructure investment we've made in our email program.
Step 5: Craft High-Performing Email Content
Technical excellence is just the beginning. Exceptional content is what drives recipients to take action. Once we've set up authentication and list hygiene, our email campaign's success hinges on the quality of our messages. Modern AI-powered filters examine tone, structure, and clarity, going beyond simple keyword detection.
Emails that feel human and purposeful outperform those focused solely on volume. We must prioritize clear value in the first screen, create scannable content with accessible design, and ensure mobile responsiveness. Content quality has become the ultimate differentiator in crowded inboxes, where technical requirements are merely the baseline.
Writing Subject Lines That Boost Email CTR Performance
Our subject line determines whether our carefully crafted content ever gets seen. This single line of text is perhaps the highest-leverage element in email marketing, as it must accomplish multiple goals simultaneously. We need to capture attention in a crowded inbox, accurately represent our email content, and compel recipients to open.
Effective subject lines build trust while creating curiosity. They should avoid deceptive practices that lead to spam complaints while standing out visually and emotionally. The best subject lines balance intrigue with transparency, giving recipients a reason to engage without misleading them about what's inside.
We should focus on these core principles when crafting subject lines:
- Keep length under 50 characters to avoid mobile truncation
- Create genuine curiosity without clickbait tactics
- Use personalization based on actual recipient data
- Test different approaches systematically
- Align subject line with email body content
Testing Subject Line Length and Emojis
Understanding what resonates with our specific audience requires systematic testing. General best practices suggest keeping subject lines under 50 characters, but we should verify whether our audience responds better to short, punchy lines or slightly longer, more descriptive ones. Mobile devices display approximately 30-40 characters before truncation occurs.
Emoji usage can increase open rates by adding visual interest and emotional context. A single relevant emoji at the beginning or end of our subject line can make our message stand out in a text-heavy inbox. Overuse appears unprofessional and can trigger spam filters in some email clients.
We recommend testing these emoji strategies:
- No emoji baseline to establish control metrics
- Single emoji at the start for immediate visual impact
- Single emoji at the end for subtle enhancement
- Category-relevant emojis that match our industry
- Seasonal or event-based emojis for timely campaigns
Personalization Techniques
Personalization goes far beyond simply inserting the recipient's first name. While "Hi [FirstName]" can be effective, more sophisticated personalization references past behavior, location, or specific interests. Behavioral personalization significantly outperforms basic merge fields because it demonstrates genuine understanding of recipient needs.
We should test personalized versus generic subject lines systematically. Personalization effectiveness varies significantly by audience and industry, so what works for B2C retail may not work for B2B services. Examples include "Based on your recent purchase of [Product]..." or "New [ProductCategory] arrivals in [City]."

Designing Engaging Email Body Content
Most recipients scan, not read, making visual hierarchy and scannability key. Our content must deliver value immediately and guide the eye naturally through our message. We should structure our emails with clear sections, use white space generously, and ensure our most important information appears early.
The first screen, what recipients see without scrolling, determines whether they engage further. We must hook readers immediately with relevant, valuable content that speaks directly to their needs or interests. Every element should serve a clear purpose in moving recipients toward our desired action.
Balancing Text and Images
Finding the right text-to-image ratio is critical for both engagement and deliverability. Emails that are entirely image-based often trigger spam filters and fail to render properly in many email clients. Text-only emails can appear less engaging and may not capture attention effectively.
We should aim for a 60:40 or 70:30 text-to-image ratio. This ensures our core message is conveyed through text even if images don't load, which happens frequently in corporate environments with strict security settings. Images should enhance and illustrate our message, not carry it entirely.
Best practices for image integration include:
- Always include descriptive alt text for accessibility
- Optimize image file sizes for fast loading
- Use images that support your message, not generic stock photos
- Test image placement to maximize email ctr performance
Creating Clear Calls-to-Action
Our call-to-action should be impossible to miss and easy to act upon. We need prominent buttons, not just text links, with action-oriented language that tells recipients exactly what happens next. "Get Your Free Guide" outperforms "Click Here" because it specifies the value and outcome.
Visual design matters a lot for CTA effectiveness. We should use contrasting colors that stand out from our email background while remaining consistent with our brand. Limiting ourselves to one primary CTA per email avoids decision paralysis and keeps recipients focused on our main objective.
Button design specifications should include:
- Minimum 44x44 pixel tap target for mobile devices
- High-contrast colors that pass accessibility standards
- Action-oriented text that begins with verbs
- Adequate white space around the button
- Placement above the fold when possible
Optimizing for Mobile Devices
Mobile optimization is non-negotiable, as 60-70% of email opens now occur on mobile devices. Recipients who have poor mobile experiences rarely give second chances, making responsive design essential for maintaining email campaign performance. Our templates must adapt gracefully to different screen sizes while maintaining readability and functionality.
We must keep our most important content and CTA above the fold, visible without scrolling. Mobile screens display far less content initially than desktop monitors, so front-loading value is critical. Use larger font sizes with a minimum of 14px for body text to ensure readability on smaller screens.
Mobile-specific considerations include:
- Single-column layouts that stack naturally
- Touch-friendly button sizes and spacing
- Compressed images that load quickly on cellular networks
- Simplified navigation that works with thumb gestures
- Testing across multiple devices and email clients
We should preview our emails on actual devices before sending. Emulators help but don't capture the real user experience of checking email on a commute or during brief moments throughout the day. Understanding how recipients actually consume our content shapes better design decisions.
A/B Testing Your Email Elements
Systematic testing is the only way to truly understand what drives email ctr performance for our specific audience. Every assumption should be validated with data, as what works for other companies may not work for ours. We should establish a structured testing program that evaluates one variable at a time to isolate what's actually making a difference.
Testing requires statistically significant sample sizes to produce reliable results. Small tests with insufficient data lead to false conclusions that can damage performance. We typically need at least 1,000 recipients per variation to achieve statistical confidence, though larger lists provide more reliable insights.
Priority elements to test systematically include:
- Subject line variations (length, tone, personalization)
- Send time and day of week
- From name and sender address
- Email content length and structure
- CTA placement, color, and copy
- Image versus text-heavy approaches
- Personalization depth and type
Documenting our test results builds organizational knowledge over time. We should maintain a testing log that records what we tested, the results, and our interpretation. This prevents repeating failed tests and helps new team members understand what resonates with our audience.
Every email campaign is an opportunity to learn. We should view testing not as an occasional activity but as an ongoing commitment to improvement. Small, incremental gains from continuous testing compound over time into dramatically better email campaign performance and stronger relationships with our recipients.
Step 6: Master Timing and Frequency for Better Engagement
Mastering the timing of our emails is key to transforming good campaigns into great ones. Sending messages when our audience is most receptive can make all the difference. Yet, sending emails at 3 AM or bombarding subscribers with daily messages they don't want can be disastrous. Understanding that timing and frequency are critical to email campaign success is essential. They often have a bigger impact than tweaks to subject lines or design.
Finding the right timing is not a one-size-fits-all solution. Each audience has its own unique engagement patterns, shaped by their behaviors, time zones, and daily routines. By analyzing these patterns, we can ensure our messages reach our audience at the perfect moment, avoiding the noise of competing emails.
Determining Optimal Send Times for Your Audience
To find the best send times, we need to analyze our subscribers' past behavior. While industry benchmarks can provide a starting point, our audience's actual behavior is far more important. Segmenting our analysis by time zone is also vital to avoid sending emails at inconvenient times for different regions.
Research indicates that B2B emails perform best on Tuesdays, Wednesdays, and Thursdays between 10 AM and 2 PM when professionals are most likely to check their emails. In contrast, B2C audiences tend to engage more in the evenings, between 7 PM and 9 PM, when they are relaxing at home. Weekend emails can also be effective for certain consumer segments, such as retail, entertainment, and lifestyle brands.

While these benchmarks can guide us, we should never follow them blindly. Our approach should include:
- A/B testing different send times with identical content to isolate timing's impact
- Analyzing engagement patterns across days of the week and hours of the day
- Segmenting analysis by subscriber characteristics like industry, role, or location
- Implementing send-time optimization features that use machine learning to deliver each message when individual recipients are most likely to engage
Many modern email service providers offer predictive send-time optimization. This technology automatically schedules delivery based on each subscriber's historical engagement patterns. It removes guesswork and continuously improves as it learns from ongoing behavior.
Finding the Right Emailing Frequency
Determining how often to email is just as critical as timing. Sending too frequently can harm our sender reputation and subscriber satisfaction. On the other hand, sending too rarely means we lose engagement. We should start with a consistent, conservative frequency and adjust based on engagement.
One value-focused email per week is a solid baseline for most audiences, providing regular touchpoints without overwhelming inboxes. It's important to note that frequency should never be one-size-fits-all. Different subscribers have different tolerance levels based on their engagement history and relationship with our brand.
"The biggest mistake in email marketing is treating your entire list the same. High-value engaged subscribers want more from you, while less engaged contacts need breathing room to rediscover why they subscribed."
Segmenting by Engagement Level
We should create engagement-based segments that receive different emailing frequencies tailored to their demonstrated interest level. This approach maximizes email campaign performance by giving engaged subscribers more of what they want while protecting relationships with less active contacts.
Our segmentation strategy should include these tiers:
- Highly engaged subscribers (opened or clicked in last 14 days): 2-3 emails per week with priority content and offers
- Moderately engaged subscribers (opened or clicked in last 30 days): Weekly emails with core content
- Low engagement subscribers (opened or clicked in last 90 days): Bi-weekly or monthly emails focusing on highest-value content
- Inactive subscribers (no engagement in 90+ days): Enter re-engagement workflow before being suppressed
This tiered approach ensures we're maximizing visibility with our most interested audience while avoiding the fatigue that pushes marginal subscribers toward unsubscribing or marking us as spam.
Monitoring Fatigue Signals
We must watch for clear indicators that we've crossed into over-sending territory. Email fatigue manifests through specific metric changes that should trigger immediate frequency reductions. The key is catching these signals early before they significantly damage our sender reputation.
Critical fatigue signals include:
- Declining open rates over time even as list size remains stable or grows
- Increasing unsubscribe rates specially immediately following sends
- Rising spam complaint rates indicating subscribers feel overwhelmed
- Decreasing click-to-open rates suggesting people open out of habit but find content less relevant
When we spot these warning signs, we should immediately reduce frequency and focus on improving content relevance. We cannot "email our way out" of engagement problems by simply sending more messages with different subject lines.
Implementing Smart Re-Engagement Campaigns
Before removing inactive subscribers, we should give them a final opportunity to indicate they want to hear from us. Smart re-engagement campaigns serve as a last-chance mechanism that actually improves our overall email campaign performance by clarifying who genuinely wants our content.
An effective re-engagement campaign typically consists of 2-3 emails sent over 2-4 weeks. These messages should feature compelling subject lines like "We miss you" or "Should we stay in touch?" that acknowledge the subscriber's inactivity without being guilt-inducing. We must offer clear value to return, such as exclusive content, special discounts, or updated content preferences.
Each re-engagement email should include a direct link to our preference center where subscribers can adjust frequency or content types without unsubscribing completely. This approach often recovers subscribers who simply felt overwhelmed by our previous cadence. We should also make the unsubscribe option easy and guilt-free because subscribers who don't want our emails actively hurt our sender reputation.
After our re-engagement campaign concludes, we must suppress all non-responders completely. Continuing to email people who never engage is the fastest way to damage deliverability for the subscribers who actually want to hear from us. Removing these inactive contacts improves our sender reputation, increases our overall engagement rates, and ensures inbox providers view our future emails more favorably.
Step 7: Navigate Email Provider-Specific Requirements
Delivering emails to various providers requires tailored strategies. Each major email provider has unique filtering algorithms and deliverability standards. Understanding these requirements is key to achieving maximum inbox placement.
What works for Gmail might not work for Outlook. We must monitor deliverability by provider, not just overall performance. This approach helps us address specific issues with targeted solutions.

Meeting Gmail Deliverability Standards
Gmail accounts make up 30-40% of most email lists in the U.S. market. This makes Gmail's deliverability standards critical for success. Gmail uses AI to evaluate sender reputation, engagement history, and content quality.
Gmail's filters consider user behavior. They track whether users mark our messages as important or delete them. These actions influence future inbox placement decisions.
Gmail's Sender Guidelines for 2026
Gmail has tightened requirements for bulk senders in 2026. All senders of 5,000 or more messages daily must have full SPF, DKIM, and DMARC authentication. These protocols verify our legitimacy.
We must implement one-click unsubscribe within 48 hours. Gmail enforces a spam complaint rate below 0.3%, aiming for 0.1%. Exceeding these limits can harm our sender reputation.
Success with Gmail depends on focusing on engagement metrics. We should only send to subscribers who have recently interacted with our content. Personalizing messages based on individual preferences helps maintain strong engagement signals.
Avoiding Gmail's Spam Filters
Gmail learns from user behavior over time. When users mark our emails as spam, future messages get filtered. This creates a dangerous feedback loop that can devastate deliverability.
We should use Gmail Postmaster Tools to monitor our domain reputation. This service provides valuable insights into how Gmail views our sending practices. Regular monitoring helps identify and correct problems before they become major issues.
Maintaining impeccable technical authentication is essential for Gmail deliverability. We must ensure our SPF records, DKIM signatures, and DMARC policies align with Gmail's requirements.
Optimizing for Outlook and Microsoft 365
Microsoft's email infrastructure presents different challenges compared to Gmail. Outlook and Microsoft 365 focus on security and protection against phishing attacks. This means we face stricter scrutiny of our links, sender patterns, and content structure.
Outlook's Junk Mail Filters
Outlook's junk mail filters are sensitive to suspicious links and unusual sender patterns. The system flags content resembling known phishing templates aggressively. We must ensure our sender name and email address remain consistent across all campaigns.
Avoiding urgent language that mimics security alerts is critical for Outlook deliverability. Phrases like "Your account will be closed" trigger filters designed to protect users from phishing attempts. We should craft our messaging to inform recipients without alarming them.
Microsoft provides Smart Network Data Services (SNDS) to monitor our IP reputation. This service shows how Microsoft's filters treat our mail and provides early warnings about deliverability problems.
Microsoft's Security Requirements
Microsoft implements SmartScreen filtering that checks our URLs against databases of known malicious sites. We should never use URL shorteners like bit.ly in emails to Outlook users. These shortened links are often blocked automatically because they obscure the true destination.
All links in our emails must use HTTPS instead of HTTP. This encryption standard signals to Microsoft's filters that we're following current security best practices. Mixed content that combines secure and insecure elements raises red flags in the filtering system.
We must maintain consistent sending patterns that don't trigger Microsoft's anomaly detection systems. Sudden spikes in volume or dramatic changes in content structure can cause temporary filtering while the system evaluates whether we've been compromised.
Yahoo Mail Best Practices
Yahoo was among the first major providers to strictly enforce DMARC requirements. The platform maintains very low tolerance for complaints and expects senders to demonstrate high list hygiene standards. Understanding Yahoo's unique approach helps us avoid common pitfalls that damage deliverability.
Yahoo requires full DMARC alignment, meaning our From domain must match our SPF and DKIM domains. Misalignment between these authentication elements results in automatic filtering or rejection. We should verify our DMARC configuration for Yahoo recipients.
The platform processes spam complaints aggressively, often blocking senders with complaint rates above 0.1%. This threshold is significantly stricter than most other providers. Yahoo has been known to implement severe filtering for senders who don't maintain proper list hygiene practices.
Yahoo users tend to report spam more frequently than Gmail or Outlook users. This behavioral difference means we must be extra careful about sending frequency and content relevance to Yahoo addresses. Segmenting our Yahoo subscribers and monitoring their engagement separately helps prevent complaint rate problems.
Delivering to GMX and Regional Email Providers
GMX and other regional email providers present unique challenges based on their geographic markets and cultural expectations. GMX, popular in Germany and parts of Europe, has strict filtering that emphasizes user privacy. The platform demonstrates low tolerance for bulk sending that doesn't meet explicit consent standards under GDPR.
We should research the specific requirements of any email provider representing more than 5% of our list. Different regions enforce distinct regulatory requirements and cultural expectations for email marketing. What works perfectly in the United States might violate regulations or cultural norms in European or Asian markets.
Regional providers often implement filtering rules based on local spam complaints and user expectations. We must monitor deliverability to these providers separately and adjust our approach based on their unique filtering characteristics. This might mean different sending frequencies, content styles, or authentication requirements.
The critical insight is that provider-specific monitoring reveals problems that overall metrics mask. When we segment our analytics by email provider, we can identify whether poor performance stems from a specific platform's filtering or reflects broader campaign issues. This granular approach enables targeted solutions that improve results across all providers.
Step 8: Monitor and Improve Email Campaign Performance
Transforming email marketing into a data-driven science requires tracking the right metrics. We must monitor deliverability, engagement, and business impact comprehensively. Without systematic measurement, we're flying blind, missing opportunities to optimize our campaigns.
The most successful email marketers create feedback loops to continuously reveal what works and what doesn't. This systematic approach to measuring performance separates industry leaders from those struggling with declining results.
Tracking Email Deliverability Performance Metrics
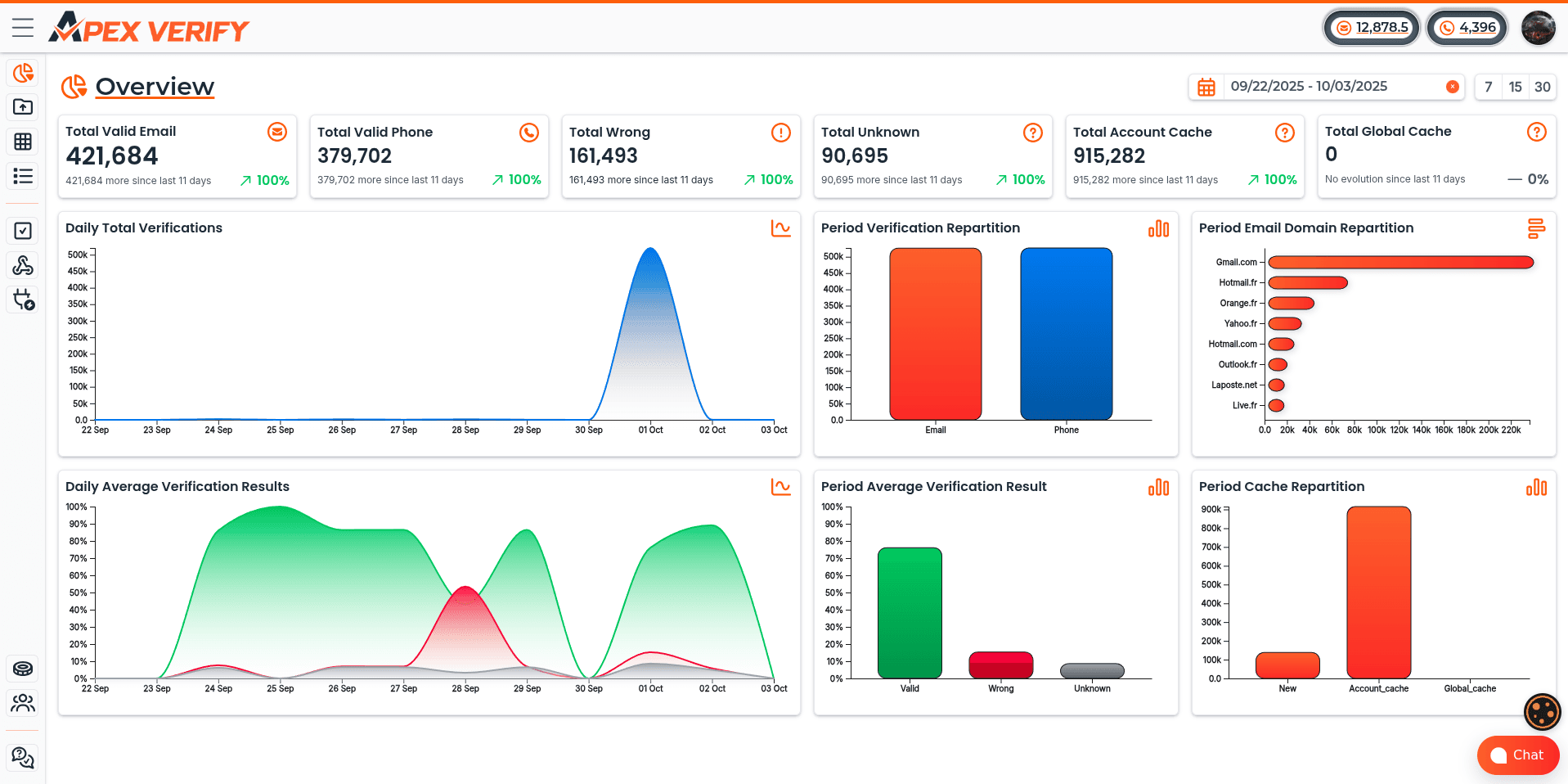
Before measuring engagement, we must ensure our emails reach recipient inboxes. Email deliverability performance is the foundation of all other metrics. Even compelling content generates zero results if it lands in spam folders.
We should monitor our delivery rate as the first indicator of list health. This metric represents emails sent minus bounces. We should target 98% or higher. Anything below 95% signals serious list quality issues that require immediate attention.
Inbox Placement Rate
Inbox placement rate is our most critical deliverability metric. It measures the percentage of delivered emails that reach the primary inbox versus being filtered. Unfortunately, this metric is difficult to measure without specialized tools.
We typically need third-party seed list services that place test addresses across major providers. These services report exactly where our emails land. We should target 95% or higher inbox placement rate. Any decline below 85% indicates serious problems requiring immediate investigation.
Major email testing platforms like Litmus and Email on Acid offer inbox placement tracking. These tools send our campaigns to test accounts across Gmail, Outlook, Yahoo, and other providers. They then report back with precise placement data that our ESP cannot provide on its own.
Bounce Rate Analysis
Bounce rates help us understand delivery failures and maintain list health. We must track hard bounces separately from soft bounces, as they require different responses. Hard bounces represent permanent failures due to invalid addresses, while soft bounces indicate temporary issues like full inboxes.
We should maintain hard bounce rates below 2% for healthy lists. Any addresses that hard bounce must be removed immediately, as continuing to send to them damages our sender reputation. If we see bounce rate spikes, we need to investigate whether the problem is concentrated among addresses from a particular source or a specific domain.
"You can't manage what you don't measure, and you can't improve what you don't manage."

Measuring Email CTR Performance
Beyond deliverability, we need to understand how recipients interact with our content. Email CTR performance tells us whether our messages resonate with our audience. Raw click-through rate provides a baseline, but deeper metrics reveal the full story.
We calculate basic CTR by dividing total clicks by delivered emails. Industry benchmarks suggest 2-5% is typical, though this varies significantly by industry and audience type. B2B audiences often show lower CTRs than B2C, while highly engaged segments perform better than general lists.
We should track which specific links in our emails receive the most clicks. This data reveals what content types and offers generate the most interest. Heat map tools show us exactly where recipients click, helping us optimize layout and design.
Click-to-Open Rate (CTOR)
Click-to-open rate is more revealing than raw CTR because it measures how effectively our content converted people who actually opened the email. We calculate CTOR by dividing unique clicks by unique opens. A good CTOR typically ranges from 20-30%, meaning about one in four people who opened our email found it compelling enough to click.
Low CTOR with high open rates suggests our subject line over-promised and our content under-delivered. High CTOR indicates strong content relevance. This metric helps us separate subject line effectiveness from content quality.
Conversion Tracking
Conversion tracking takes us beyond engagement to business impact. We must implement proper tracking pixels and UTM parameters on all email links so we can definitively attribute website actions back to specific campaigns. These actions include purchases, form submissions, downloads, and other valuable behaviors.
We should calculate conversion rate by dividing conversions by delivered emails. We also need to track revenue per email, which equals total revenue divided by delivered emails. For promotional campaigns, these metrics directly tie our email efforts to business results.
The average email marketing ROI ranges from $36-$45 per $1 spent, making it one of the highest-performing digital channels. This varies widely based on industry, audience quality, and execution. Tracking our specific ROI helps us justify email program investments and identify improvement opportunities.
Using Analytics to Identify Improvement Areas
We need to review metrics not just in isolation but in combination to diagnose specific problems. Pattern recognition across multiple metrics reveals root causes better than single data points. This analytical approach transforms raw data into actionable insights.
High open rates but low CTOR suggest content relevance issues. Our subject lines are working, but our email body isn't delivering on the promise. High CTOR but low conversion rate indicates landing page problems, not email issues.
Increasing unsubscribe rates point to frequency or relevance issues. We might be sending too often or to poorly segmented audiences. Declining inbox placement suggests authentication or reputation problems that require technical investigation.
We should conduct thorough campaign retrospectives within 48 hours of each major send. Document what worked and what didn't while the campaign is fresh. These post-mortems become invaluable references for future campaigns.
Setting Up Performance Dashboards
Performance dashboards bring all our critical metrics into a single view. They allow us to monitor email campaign performance at a glance and quickly spot concerning trends. A well-designed dashboard saves hours of manual reporting while ensuring nothing slips through the cracks.
Our dashboard should include four categories of metrics:
- Deliverability metrics: Delivery rate, bounce rate, spam complaint rate
- Engagement metrics: Open rate, CTR, CTOR, unsubscribe rate
- Business metrics: Conversion rate, revenue per email, ROI
- List health metrics: List growth rate, engagement segments, inactive subscriber percentage
We should review dashboards weekly at minimum, with daily monitoring during high-volume campaigns. Most email service providers offer basic dashboards, but integrating our email data with broader marketing analytics platforms provides deeper insights.
Advanced integrations connect email performance to customer lifetime value, multi-touch attribution, and overall marketing ROI. Tools like Google Analytics, Tableau, or dedicated marketing analytics platforms aggregate data across channels. This holistic view shows how email fits into the larger customer journey.
The goal is creating a closed feedback loop where we continuously monitor performance, identify specific opportunities, implement changes, and measure impact. This iterative approach drives consistent improvement in email deliverability performance and overall campaign results over time.
Step 9: Implement Advanced Optimization Strategies
The gap between good and exceptional email campaign performance often hinges on advanced optimization strategies. These sophisticated techniques demand more powerful platforms and deeper data integration. Yet, they significantly boost engagement and conversion rates. We're moving beyond basic personalization, embracing artificial intelligence, behavioral prediction, and dynamic content for truly individualized experiences.
Advanced optimization is the competitive edge in 2026 email marketing. While basic best practices become standard, the most successful marketers stand out through intelligent automation and precision targeting. Each message feels custom-crafted for its recipient.
Leveraging AI and Machine Learning for Personalization
Modern artificial intelligence revolutionizes personalization in our campaigns. We're no longer limited to inserting a first name in the subject line. Today's AI analyzes individual subscriber behavior patterns to predict future actions and preferences with remarkable accuracy.
Machine learning models examine which products each subscriber is most likely to purchase based on browsing history, past purchases, and behavioral signals. These systems can recommend products that consider not just what someone bought before, but what items are frequently purchased together and what browsing patterns indicate emerging interest.
AI-powered personalization capabilities include:
- Predictive product recommendations based on behavioral analysis
- Automated content optimization that learns from each campaign
- Subject line generation with performance prediction
- Tone and messaging adaptation to individual personality profiles
- Optimal offer selection based on likelihood to convert
We can implement AI copywriting assistance that generates subject line variations optimized for our goals. Whether it's maximizing opens, clicks, or conversions. Some platforms now offer machine learning models that automatically test variations and learn which approaches work best for specific subscriber segments, continuously improving without manual intervention.
The key to successful AI implementation is providing quality data. Our machine learning models are only as good as the information they analyze. This means maintaining clean data and tracking meaningful behavioral signals becomes increasingly important.
Implementing Progressive Profiling
Progressive profiling allows us to build subscriber profiles gradually without overwhelming new subscribers with lengthy forms. Instead of requesting ten pieces of information at signup, we ask for just the essentials initially. Then, we gather additional data over time through subsequent interactions.
This approach respects subscriber attention while systematically building detailed profiles for sophisticated personalization. Each email interaction, preference center visit, and behavioral signal adds valuable data to the subscriber's profile.
- Explicit preferences shared through forms and preference centers
- Behavioral data from email engagement patterns
- Content preferences based on click-through behavior
- Purchase history and transaction patterns
- Temporal patterns showing optimal engagement windows
We track which email categories subscribers click most frequently, what time they typically engage with messages, what content length they prefer, and which offers generate interest. This accumulated intelligence enables personalization that feels helpful, not intrusive, because subscribers have voluntarily shared preferences through their actions.
The gradual nature of progressive profiling also improves data quality. When we ask for information at relevant moments, like requesting birthday information near a holiday promotion, or asking about product preferences after someone browses specific categories, we receive more accurate responses and higher completion rates.
Using Predictive Send Time Optimization
Predictive send time optimization leverages machine learning to determine the optimal delivery time for each individual subscriber. Instead of sending to our entire list simultaneously, we deliver messages when each recipient is most likely to engage.
These systems analyze historical engagement patterns to identify when each person typically opens emails. Someone who checks email at 6 AM receives our message then, while another subscriber who engages most at 8 PM gets the same email in the evening.
"Predictive send time optimization can improve open rates by 5-20% by ensuring emails arrive when recipients are most likely to be checking their inbox."
This strategy recognizes that optimal send times vary dramatically between individuals. The traditional approach of finding the "best time" for our entire audience leaves massive engagement opportunities on the table because no single time works for everyone.
Modern predictive systems consider multiple factors including day of week preferences, typical wake and sleep patterns, work schedule indicators, and even real-time factors like whether someone has recently engaged with our brand through other channels.
Implementation requires email platforms with sophisticated delivery infrastructure capable of scheduling thousands of individual send times. We also need sufficient historical data for the algorithms to identify reliable patterns, typically at least 30-60 days of engagement history per subscriber.
Creating Dynamic Content Blocks
Dynamic content blocks transform single email templates into personalized experiences by changing sections based on recipient attributes, behavior, or real-time data. Instead of creating completely different emails for different segments, we build one template that displays relevant content to each viewer.
Our promotional email might show different products to different demographic groups, display regional inventory, or present different messaging to first-time buyers versus loyal customers, all within the same campaign. This approach dramatically improves relevance without multiplying our campaign management workload.
Dynamic content applications that boost email campaign performance include:
- Product recommendations based on browsing history and purchase patterns
- Location-specific offers and store information
- Testimonials matching the recipient's industry or use case
- Content blocks reflecting stated preferences or interests
- Time-sensitive offers with countdown timers personalized by timezone
The technical implementation requires clean segmentation data and email platforms supporting conditional content logic. We design templates with placeholder blocks that pull specific content based on data field values associated with each recipient.
Testing dynamic content requires thoughtful planning. We need to verify that all possible content combinations render correctly and that our fallback content works properly when specific data points are missing for some subscribers.
Testing Advanced Segmentation Strategies
Advanced segmentation moves beyond basic demographic splits to behavioral and predictive segments that better represent subscriber intent and likelihood to convert. These sophisticated approaches require deeper analytics but deliver substantially better engagement and conversion rates.
Advanced segmentation strategies we should test:
- Engagement velocity: Grouping subscribers by how quickly engagement has increased or decreased over time
- Predictive lifetime value: Identifying subscribers likely to become high-value customers based on early behavioral signals
- Content preference clusters: Creating segments of subscribers with similar content interaction patterns
- Micro-moment triggers: Sending based on specific behavior combinations like viewing products multiple times without purchasing
- Risk-of-churn scoring: Identifying subscribers showing early warning signs of disengagement
Trend data from 2026 shows significant growth in AI-assisted segmentation and predictive modeling. Email providers now place heavier weighting on user behavior signals, including delete-without-read actions, which makes behavioral segmentation increasingly important for maintaining strong deliverability.
We should continuously test new segmentation hypotheses against our baseline segments. Not every advanced segmentation strategy will outperform simpler approaches for every business, so controlled testing helps us identify which sophisticated segments deliver meaningful improvements for our specific audience.
Each of these advanced strategies requires strong data infrastructure and sophisticated email marketing platforms. They represent the competitive edge in email campaign performance as basic best practices become universal and the most successful marketers pull ahead through personalization and automation that delivers individually relevant experiences at scale.
Conclusion
Email remains a powerhouse, delivering $36-$45 in ROI for every $1 invested, but only if messages reach engaged subscribers. Strong email deliverability is a testament to trust and consistency. It rewards those who prioritize long-term success, respect engagement, and create content that earns attention.
The inbox now belongs to the subscriber. Our role is to earn our spot through clean data, an engagement-first strategy, and continuous optimization. Email campaign performance flourishes when we focus on building genuine relationships, not just technical fixes.
We've outlined the essential system for success in 2026. From email verification and authentication to SMTP configuration and content optimization, each part builds subscriber trust. Providers reward this effort with better inbox placement.
Email marketing success is an ongoing journey, not a one-time achievement. There's always room to enhance verification, refine segmentation, or explore new content approaches. By striving for excellence in email deliverability and optimizing every aspect of our program, we unlock email marketing's full power. This will drive sustainable business growth in 2026 and beyond.
Frequently Asked Questions
What is the most important factor affecting email deliverability in 2026?
The most important factor is subscriber engagement. Email providers like Gmail, Outlook, and Yahoo now use sophisticated machine learning algorithms. These algorithms prioritize how recipients interact with our messages, opens, clicks, replies, and forwards signal positive intent. On the other hand, deletions, spam complaints, and inactivity damage our sender reputation.
Technical authentication (SPF, DKIM, DMARC) is the baseline requirement. But engagement metrics ultimately determine whether our emails consistently reach the inbox. This means we must focus on sending relevant, valuable content to subscribers who genuinely want to hear from us.
How does email verification improve our email campaign performance?
What's the difference between SPF, DKIM, and DMARC authentication protocols?
What are spam traps and how can we avoid hitting them?
Why is SMTP configuration important for email deliverability?
How do we write subject lines that improve email CTR performance?
How does Gmail's deliverability requirements differ from other email providers?
Should we use email verification software or email verification SaaS?
What is IP warming and why is it necessary?
What are the consequences of hitting a Spamhaus blocklist?
How can we use Gmail Postmaster Tools to improve deliverability?
What are the key differences between email verification tools and manual list cleaning?
What is the role of AI in modern email marketing optimization?